P2P IoT: Secure & Efficient Device Networking [Explained]
Are you ready to unlock the true potential of your IoT devices? The future of IoT lies in Peer-to-Peer (P2P) networking, offering unparalleled efficiency, security, and control.
The Internet of Things (IoT) has rapidly evolved from a futuristic concept to an integral part of our daily lives. From smart homes to industrial automation, IoT devices are transforming how we interact with the world around us. However, as the number of connected devices continues to skyrocket, traditional centralized network architectures are struggling to keep pace. This is where Peer-to-Peer (P2P) networking emerges as a game-changing solution, offering a decentralized and efficient approach to managing the ever-expanding IoT ecosystem. Sensor nodes, the workhorses of the IoT environment, are now empowered by P2P networking, creating a dynamic and interconnected web of devices.
| Feature | Description |
|---|---|
| Scalability | P2P networks easily accommodate the growing number of IoT devices without performance bottlenecks. |
| Reduced Latency | Direct device-to-device communication minimizes delays, crucial for real-time applications. |
| Fault Tolerance | The absence of a central server eliminates single points of failure, enhancing network resilience. |
| Bandwidth Efficiency | Local data processing and direct communication reduce reliance on central servers, saving bandwidth costs. |
| Enhanced Security | Distributed data and processing make it harder for cybercriminals to compromise the network. |
Kim et al.'s pioneering work has underscored the potential of P2P computing for establishing a trusted network of personalized IoT services. Their research emphasizes the protection of both IoT service users and their sensitive data. In a world where privacy concerns are paramount, this approach offers a significant advantage over traditional centralized systems. The increasing role of IoT devices, fueled by technological advancements, necessitates innovative solutions like P2P networking to manage the sheer volume of interconnected devices efficiently and reliably.
- Husband Partner Sarah Hadland The Ultimate Guide To Her Love Life
- Popular Interview Shows Your Ultimate Guide To Mustwatch Conversations
Imagine a scenario with billions of interconnected devices. A P2P network emerges as a powerful tool for managing bandwidth and delivering quicker responses, thus making the IoT more efficient and reliable. This is especially crucial in applications where real-time data processing and immediate action are required. Think of smart homes where lighting, security, and appliances respond instantly to your commands, or industrial environments where automated systems react to sensor data with minimal delay.
Curious about securely connecting your remote IoT devices using a P2P Raspberry Pi setup without incurring costs? Prepare to be amazed! The possibilities are vast, and the benefits are undeniable. The integration of IoT with diverse equipment across various sectors has already yielded unprecedented levels of efficiency and convenience. However, critical issues such as data privacy, security vulnerabilities, and the absence of a robust framework for managing interactions remain significant challenges. P2P architecture addresses these challenges head-on, offering a decentralized and secure alternative.
The technical document introducing the IoT video P2P underlying interface outlines its usage. The IoT video P2P interface, defined in the iv_av.h file, shares a mutually exclusive usage pattern with the interface described in the "Audio and Video Transmission and Dialogue Module Description" document. Users must select one interface for audio and video transmission. When using the IoT video P2P interface, the IoT video SDK provides only basic data transmission capabilities. This streamlined approach ensures efficient resource utilization and focuses on core functionalities.
- Tony Mortimer Net Worth The Untold Story Of Success Fame And Fortune
- Beckham Infidelity The Untold Story Behind The Headlines
The concept of "IoT P2P and VPC Networks for a Smarter, Safer World" encapsulates the overarching goal of these technologies. As IoT devices become increasingly sophisticated, so too must the solutions that connect and protect them. By strategically combining remote IoT P2P and IoT VPC networks, businesses and individuals can create a highly efficient, reliable, and secure environment for all their connected devices. This synergistic approach maximizes the benefits of both technologies, providing a robust defense against potential threats while optimizing performance.
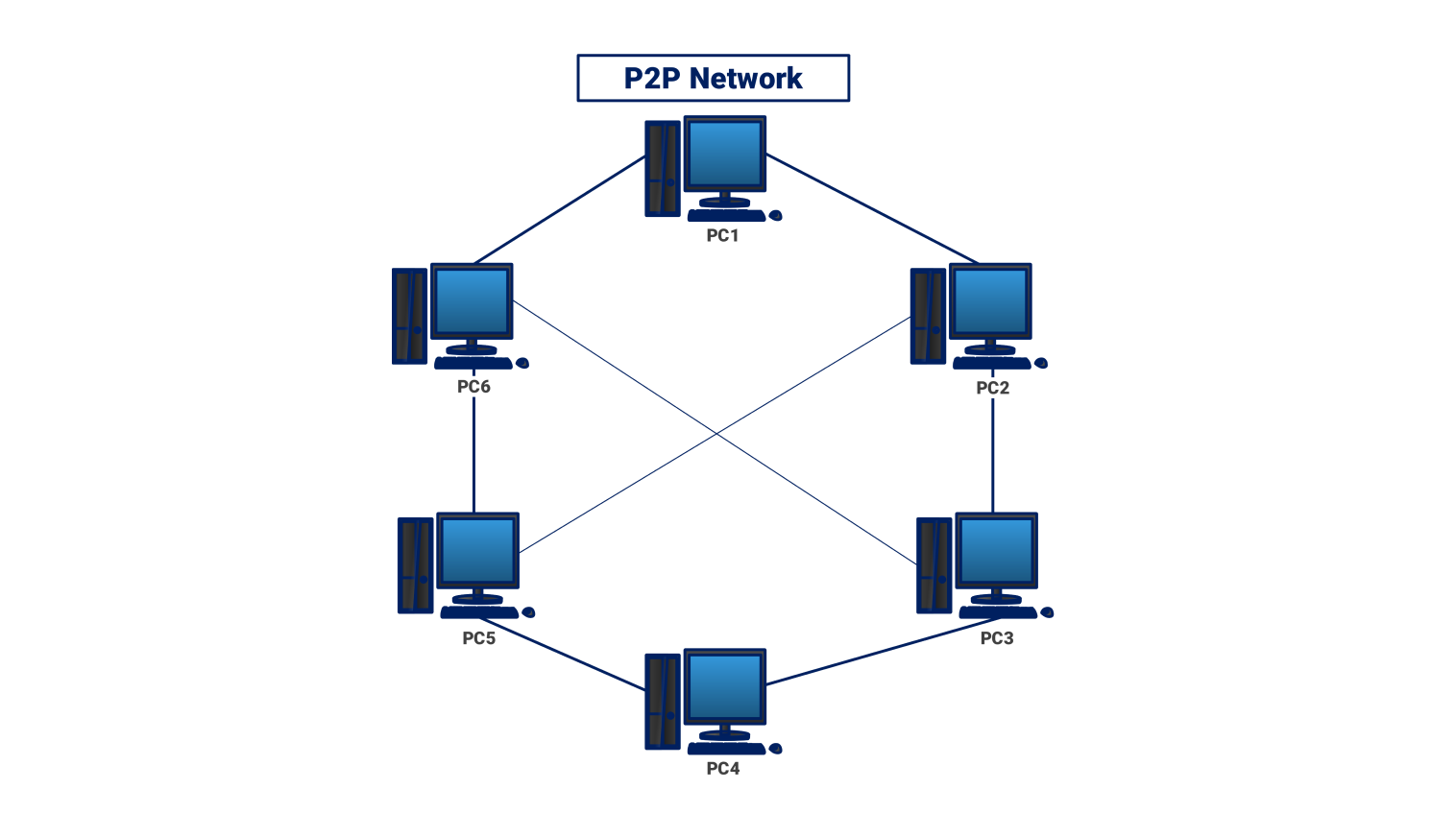
In a P2P network, each participant functions as both a client and a server, enabling direct resource and service sharing with other peers. This decentralized model eliminates the need for a central authority, promoting greater autonomy and resilience. In contrast to traditional client-server architectures, where all communication flows through a central server, P2P networks distribute the workload and responsibility across all participating devices. This distribution not only enhances performance but also improves security by eliminating single points of failure.
IoT trust management is a crucial security solution that establishes trust between different IoT entities before they engage in any interaction. This involves verifying the identity and integrity of each device, ensuring that only authorized devices can participate in the network. By implementing robust authentication and authorization mechanisms, IoT trust management mitigates the risk of malicious actors infiltrating the network and compromising sensitive data. This is particularly important in applications where data privacy and security are paramount, such as healthcare and finance.
If a peer device is configured as a router on the server side, this network configuration enables direct IP access to all devices from that server, without requiring a VPN. While this configuration offers convenience, it's less secure than a dedicated VPN tunnel. However, it still provides better security compared to running general IoT devices on a common APN. The trade-off between security and convenience is a critical consideration when designing an IoT network architecture. Organizations must carefully weigh the risks and benefits of each approach to determine the most appropriate solution for their specific needs.
In the vast realm of technological progress, the Internet of Things (IoT) has emerged as a dominant force, facilitating seamless communication among a diverse array of devices. From smart thermostats that learn your preferences to wearable fitness trackers that monitor your health, IoT devices are revolutionizing how we live and work. The convergence of these devices into interconnected networks presents both opportunities and challenges. P2P networks offer a promising solution for addressing the scalability, security, and efficiency demands of the burgeoning IoT landscape.
P2P networks find applications in file sharing, decentralized applications, and IoT systems. The versatility of P2P architecture makes it well-suited for a wide range of use cases. In file sharing, P2P networks enable users to exchange files directly with each other, without relying on a central server. In decentralized applications, P2P networks provide a secure and resilient platform for building applications that are resistant to censorship and single points of failure. In IoT systems, P2P networks facilitate direct device-to-device communication, enabling greater efficiency and autonomy.
Understanding P2P network architecture is essential for cybersecurity and network management. As P2P networks become increasingly prevalent, it's crucial for IT professionals to understand how they work and how to secure them. This includes understanding the different types of P2P networks, the security risks associated with P2P traffic, and the tools and techniques for monitoring and managing P2P traffic. By gaining a deeper understanding of P2P network architecture, organizations can better protect their networks and data from potential threats.
Emerging technologies like blockchain are leveraging P2P networks for decentralized operations. Blockchain, the technology behind cryptocurrencies like Bitcoin, relies on a P2P network to maintain a distributed ledger of transactions. This decentralized architecture makes blockchain highly resistant to tampering and censorship. As blockchain technology matures, it's expected to find applications in a wide range of industries, including supply chain management, healthcare, and finance. The synergy between P2P networks and blockchain technology is poised to drive innovation and disruption across various sectors.
P2P IoT is based on IoT VPC, and it utilizes Raspberry Pi for interaction. This combination of technologies enables the creation of powerful and flexible IoT solutions. Raspberry Pi, a low-cost and versatile single-board computer, serves as a gateway for connecting IoT devices to the P2P network. IoT VPC (Virtual Private Cloud) provides a secure and isolated environment for running IoT applications. By leveraging these technologies, developers can build P2P IoT solutions that are both powerful and secure.
A P2P IoT network enables devices to exchange resources and data while providing services without a central server. This decentralized approach fosters greater autonomy and resilience. Devices can communicate directly with each other, sharing data, processing power, and other resources. This eliminates the need for a central server to coordinate communication, reducing latency and improving efficiency. The absence of a central server also makes the network more resistant to failures and attacks.
Platforms that facilitate P2P IoT implementation offer scalability, reduced latency, and improved fault tolerance. These platforms provide the necessary infrastructure and tools for developers to build and deploy P2P IoT applications. Scalability ensures that the network can accommodate the growing number of IoT devices. Reduced latency enables real-time data processing and immediate action. Improved fault tolerance ensures that the network remains operational even if some devices fail. These features make P2P IoT platforms an attractive option for organizations looking to build robust and efficient IoT solutions.
Furthermore, when data processing occurs locally on IoT devices, P2P networks can significantly reduce bandwidth costs associated with transmitting data over the network. By processing data locally, devices can reduce the amount of data that needs to be transmitted to a central server. This not only saves bandwidth costs but also improves performance by reducing latency. This approach is particularly beneficial in applications where large amounts of data are generated, such as video surveillance and environmental monitoring.
With improved security through distributed data and processing, and high access control, P2P IoT solutions present a formidable challenge for cyber criminals aiming to steal data or compromise the network. The decentralized nature of P2P networks makes it difficult for attackers to target a single point of failure. Distributed data and processing ensure that even if one device is compromised, the attacker cannot gain access to the entire network. High access control restricts access to sensitive data and resources, further mitigating the risk of unauthorized access.
A P2P (peer-to-peer) connection establishes a direct communication infrastructure between two peers. This direct connection bypasses the need for intermediaries, streamlining communication and reducing latency. The two peers can be any type of device, such as a client device (smartphone or laptop) and an IoT device (surveillance camera, smart door lock, alarm system, heat controller, or any internet-enabled device). This direct communication channel enables real-time data exchange and remote control capabilities.
Here’s a breakdown of the critical aspects of P2P IoT platforms:
P2P platforms eliminate the single point of failure associated with centralized servers. This is a major advantage over traditional client-server architectures, where the failure of the central server can bring down the entire network. By distributing the workload and responsibility across all participating devices, P2P platforms ensure that the network remains operational even if some devices fail.
Each device within the network can communicate and share data directly with other devices. This fosters a more robust and resilient network. Direct device-to-device communication eliminates the need for intermediaries, reducing latency and improving efficiency. This also enables devices to share resources, such as processing power and storage, further enhancing the network's capabilities.
P2P IoT is well-suited for situations requiring fast and convenient device control. In scenarios where real-time responsiveness is critical, P2P networks offer a significant advantage over traditional centralized systems. The direct communication channel between devices enables immediate action and feedback, making it ideal for applications such as remote control, security monitoring, and industrial automation.
Many home IoT devices utilize P2P SMS, as do smart buildings like offices. This enables devices to send notifications and alerts directly to users' smartphones or other mobile devices. P2P SMS provides a reliable and cost-effective way to communicate with users, ensuring that they are always informed of important events. This is particularly useful for applications such as security alarms, smoke detectors, and environmental sensors.
Smoke detectors, security cameras, and other devices requiring the transmission of notifications to the end user often employ P2P SMS. This ensures that users receive timely alerts, regardless of their location. P2P SMS provides a direct and reliable communication channel, bypassing the need for intermediaries and ensuring that notifications are delivered promptly. This is crucial for applications where immediate action is required, such as responding to a fire alarm or a security breach.
In a P2P IoT network:
Nodes can share data storage, processing power, or bandwidth. This resource sharing optimizes network performance and reduces costs. Devices can contribute their unused resources to the network, creating a dynamic and efficient ecosystem. This approach is particularly beneficial in applications where resources are unevenly distributed, such as in a network of environmental sensors where some sensors may have more processing power or storage capacity than others.
Tasks or data processing can be distributed among devices to balance the load and optimize performance. This distributed processing approach enhances the network's scalability and resilience. By distributing the workload across multiple devices, the network can handle a larger volume of data and tasks without experiencing performance bottlenecks. This also ensures that the network remains operational even if some devices fail, as the workload can be redistributed to other devices.
In environmental monitoring, a temperature sensor can share its readings with neighboring sensors, creating a localized map of the area. This collaborative data sharing enhances the accuracy and granularity of the monitoring process. By combining data from multiple sensors, a more complete and accurate picture of the environment can be created. This is particularly useful for applications such as weather forecasting, pollution monitoring, and agricultural management.
The P2P process involves a network structure where each participant, known as a node, acts as both a client and a server. This eliminates reliance on a central server for resources and services. Instead, each node can trade resources and services directly with other nodes in the network. This decentralized approach fosters greater autonomy, resilience, and efficiency.
Just about every security report out there says that IoT devices should be isolated from the normal use network. This is primarily due to the difficulty in controlling or adjusting what IoT devices do on the network, especially regarding their "calling home" behavior. Many IoT devices are programmed to periodically connect to their manufacturers' servers to download updates or transmit data. This behavior can pose a security risk if the device is compromised or if the manufacturer's servers are vulnerable.
As others have mentioned, the VZ IoT SSID doesn't provide this isolation. Devices on this SSID have full access. This lack of isolation can expose the network to potential security risks, as a compromised IoT device could be used to gain access to other devices on the network. It's crucial to implement appropriate security measures, such as network segmentation and access control, to protect the network from potential threats.
Integration between the Internet of Things (IoT) and equipment across sectors has resulted in formerly unthinkable efficiency and convenience. From smart factories that optimize production processes to smart cities that improve traffic flow, IoT is transforming industries and improving the quality of life. The convergence of these technologies presents both opportunities and challenges. P2P architecture offers a promising solution for addressing the scalability, security, and efficiency demands of the burgeoning IoT landscape, particularly in addressing critical issues like data privacy, security flaws, and the lack of a reliable framework for controlling interactions.
P2P architecture can be applied in Internet of Things (IoT) networks to enable devices to communicate directly with each other, reducing latency and improving efficiency. This direct communication channel bypasses the need for intermediaries, streamlining data exchange and improving responsiveness. This is particularly beneficial in applications where real-time data processing and immediate action are required. The applications include instant messaging and voice calls:


Detail Author:
- Name : Prof. Dahlia Schroeder
- Username : buddy.jaskolski
- Email : uriah.quitzon@gmail.com
- Birthdate : 1989-04-30
- Address : 5237 Renner Causeway Lake Dillan, ME 15828-6139
- Phone : 435-403-2966
- Company : Mohr Inc
- Job : Tree Trimmer
- Bio : Ea sed ipsa et. Nisi voluptatem nostrum atque eum. Dolores animi neque et quia illo odio. Rerum non provident excepturi ducimus placeat est.
Socials
facebook:
- url : https://facebook.com/liza_murray
- username : liza_murray
- bio : Aut exercitationem illum aliquid itaque sed quia laboriosam.
- followers : 4314
- following : 1846
tiktok:
- url : https://tiktok.com/@liza_dev
- username : liza_dev
- bio : Sed perspiciatis doloremque deleniti occaecati error ad vel architecto.
- followers : 3335
- following : 131
linkedin:
- url : https://linkedin.com/in/lizamurray
- username : lizamurray
- bio : Necessitatibus ipsam totam laboriosam.
- followers : 5183
- following : 1686
instagram:
- url : https://instagram.com/lizamurray
- username : lizamurray
- bio : Asperiores velit qui est laboriosam. Blanditiis sint minima deleniti laudantium possimus eveniet.
- followers : 120
- following : 2074